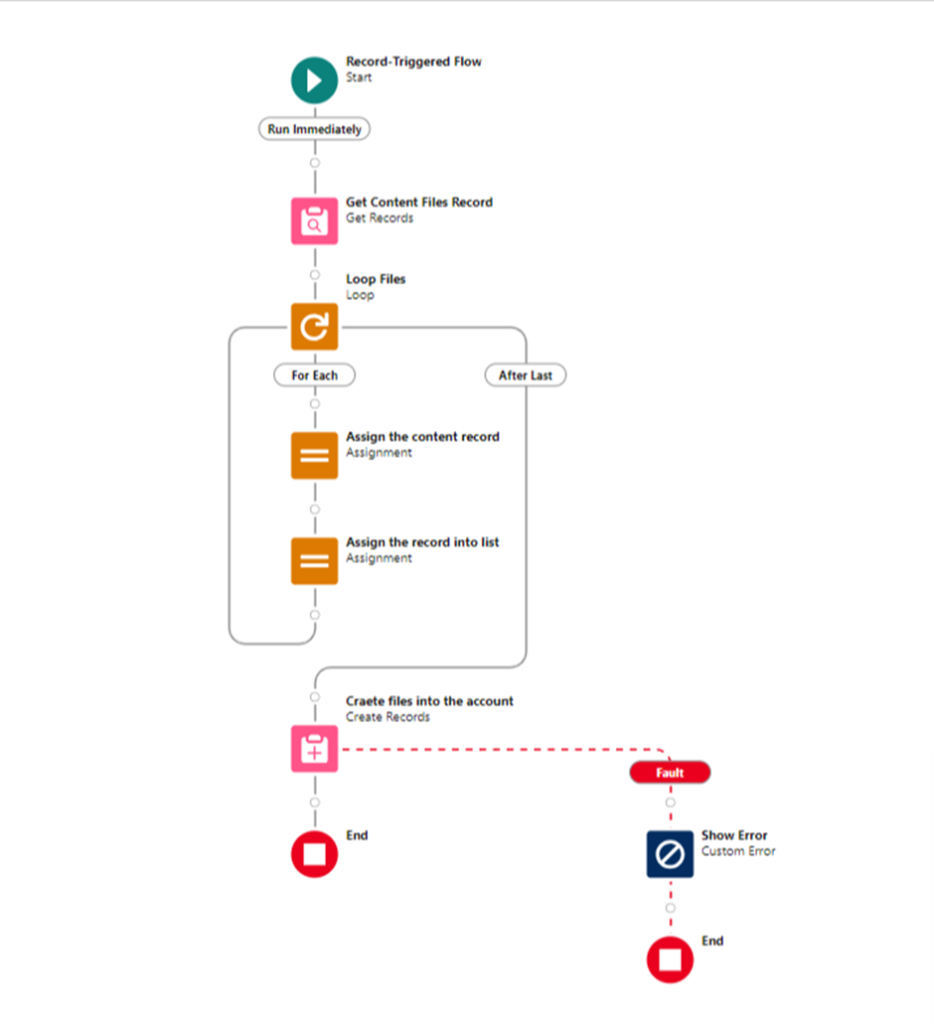
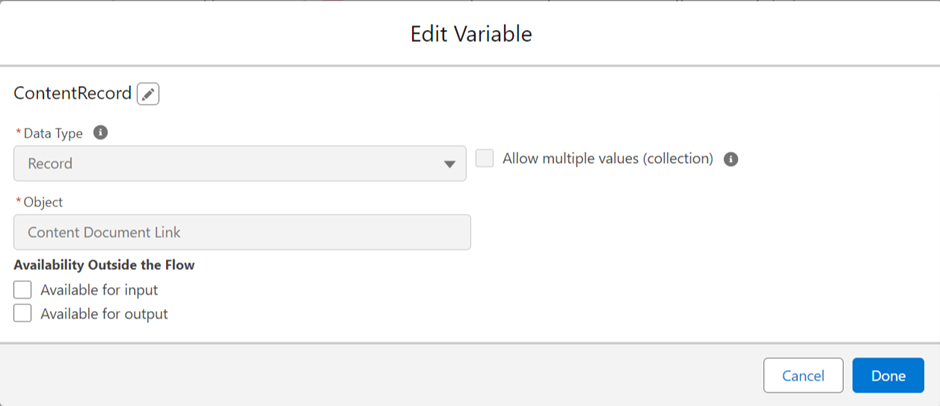
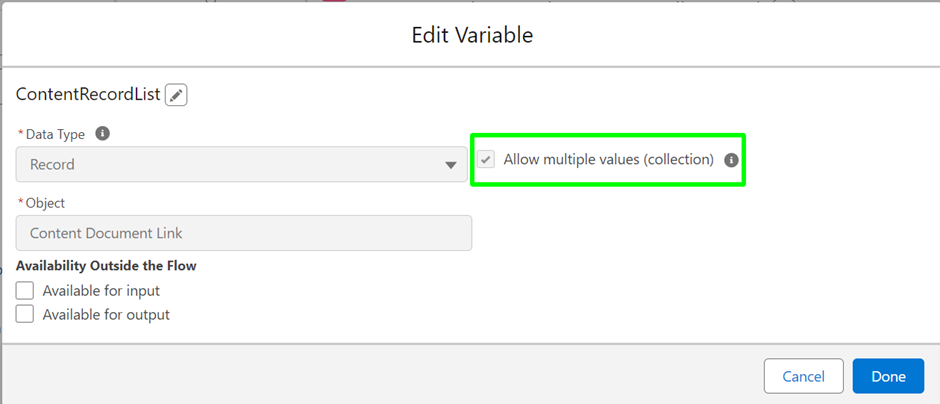
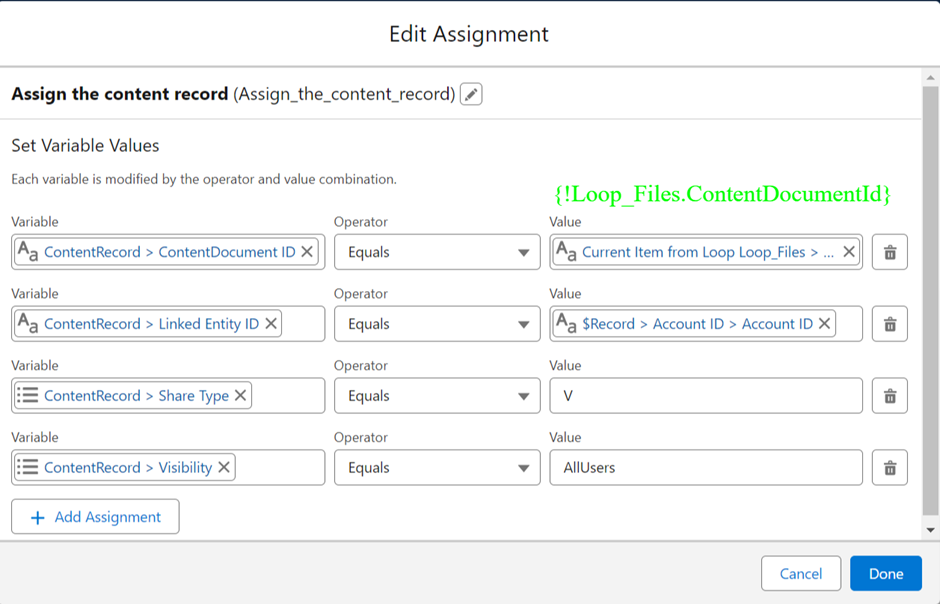
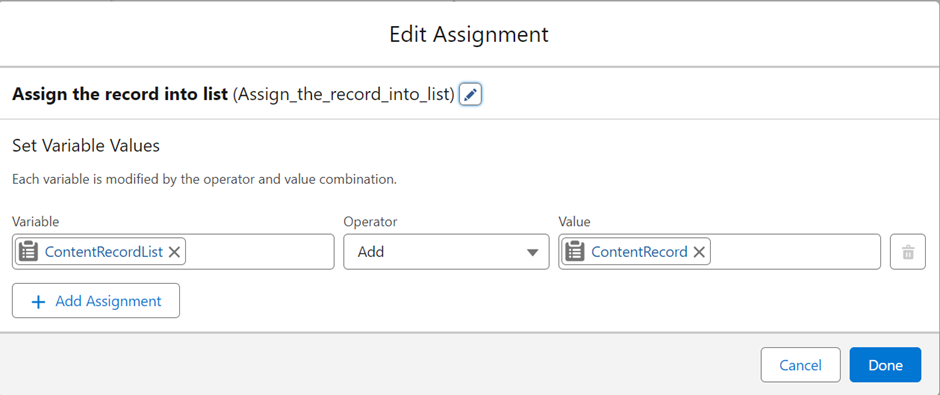
As we anticipate the Summer ’24 release in Salesforce, one feature that’s receiving a significant upgrade is Field History Tracking—an essential tool for maintaining data integrity and transparency. Let’s explore the journey of field history tracking, from its inception to the forthcoming enhancements.
Before – Field History Tracking Overview
Field History Tracking has long been a cornerstone of data management within Salesforce environments. Previously, managing Field History Tracking involved navigating through multiple menus, and making adjustments on a per-object basis. Administrators would typically access this functionality by navigating to Fields & Relationships and then to the Set History Tracking button.
While functional, this approach could be cumbersome, especially when dealing with multiple objects and fields. Despite its importance in ensuring data transparency and compliance, Field History Tracking has seen few updates in recent releases.
Now – Enhanced Field History Tracking in Summer ’24 Release
Enter the Summer ’24 release, where Salesforce unveils a revamped Field History Tracking experience. Among the notable enhancements is the introduction of a dedicated Field History Tracking page within Setup—a game-changer for administrators.
The new Setup page offers a centralized hub for managing object field histories, streamlining the configuration process, and enhancing the user experience. Gone are the days of navigating through multiple menus; now, administrators can efficiently control both tracked objects and fields from a single interface.
Upon accessing the Field History Tracking page, users are greeted with an overview of tracked objects, accompanied by a tally of the number of fields being tracked—a feature designed to provide instant visibility into data tracking configurations. From here, administrators can seamlessly update field tracking settings for multiple objects without the need to navigate to each one separately in the Object Manager.
The interface further simplifies the process by presenting the list of fields in a convenient side panel. This allows for swift modifications and adjustments, with changes easily saved before seamlessly transitioning to the next object in the main list. This streamlined workflow ensures a more efficient configuration process, saving valuable time and effort for administrators.
Considerations for Effective Implementation
While the enhanced Field History Tracking offers exciting new capabilities, it’s essential to be aware of considerations and limitations:
- Data Retention: Historical change data is retained for up to 18 months in the UI and up to 24 months via API. Extended retention is available through the purchase of Field Audit Trail.
- Field Tracking: While most standard and custom fields support comprehensive tracking, some field types may only track user and timestamp information, omitting old and new values.
- Field Limits: There’s a hard limit of 20 tracked fields per standard or custom object, extendable to 60 through the purchase of Field Audit Trail. Tasks and Events have their own tracking limitations, allowing for tracking of only six fields each.
- System Context Changes: Changes made in system context, such as through Salesforce Flows, are only tracked if the current user possesses the necessary field permissions.
Embracing Enhanced Field History Tracking
With the upcoming Salesforce Summer ’24 release, the revamped Field History Tracking promises to elevate data management capabilities within Salesforce environments. By centralizing tracking configurations and streamlining the setup process, administrators can ensure greater transparency, compliance, and data integrity throughout their CRM operations.
As organizations prepare to embrace these enhancements, it’s crucial to familiarize themselves with the new functionalities and considerations, paving the way for a seamless transition to the latest iteration of Field History Tracking in Salesforce. The dedicated setup page empowers users to efficiently manage field histories, unlocking new opportunities for data-driven decision-making and organizational growth.